HawkEye Write Up
I was able to go through the questions for this challenge in a reasonable amount of time, but writing this took a long time. It was worth it though because it forced me to look up and read blogs and watch videos about DNS, SMTP, broadcast addresses, and more! I can often muddle my way through the questions, but do not understand why the answer is right. Documenting the answers helps me to better understand.
I am just starting this learning journey with the more defensive side of cybersecurity so if there is anything incorrect or you have any suggestions then please let me know!
Website: cyberdefenders.org
Link to challenge: https://cyberdefenders.org/blueteam-ctf-challenges/91
Scenario: An accountant at your organization received an email regarding an invoice with a download link. Suspicious network traffic was observed shortly after opening the email. As a SOC analyst, investigate the network trace and analyze exfiltration attempts.
Tools Suggested: There were 3 suggestions for tools. I only used Wireshark for this challenge.
Websites I used:
References
Resources
Helpful write ups
https://maakthon.blogspot.com/2022/03/ctf-packet-analysis-hawkeye-challenge.html
https://responderj01.medium.com/hawkeye-walkthrough-cyberdefenders-aea9f0799a6b
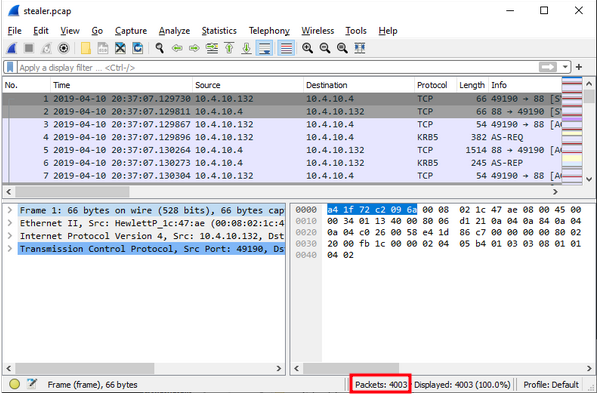
1) How many packets does the capture have?
You can see the number of packets on the status bar.
You can also go to Statistics → Capture File Properties.
4003
2) At what time was the first packet captured?
Go to View → Time Display Format → UTC Date and Time of Day to change the Time column to UTC. Then click the up button shown below, or press Ctrl + HOME, to go to the first packet.
2019-04-10 20:37:07 UTC
3) What is the duration of the capture?
Go to Statistics → Capture File Properties.
01:03:41
4) What is the most active computer at the link level?
First, let’s look at the this blog post to read more about the 7 layers of the OSI Model: https://www.bmc.com/blogs/osi-model-7-layers/.
This blog contains the following image that hints to us that maybe we should look at Ethernet endpoints.
Go to Statistics → Endpoints. We see the computer with the most activity below.
00:08:02:1c:47:ae
5) Manufacturer of the NIC of the most active system at the link level?
“A media access control address (MAC address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment.” - Wikipedia
This question is asking who the manufacturer of the NIC is for the computer in the previous question. We can figure out the manufacturer by putting the MAC address we found in the previous question into https://macvendors.com.
Hewlett-Packard
6) Where is the headquarter of the company that manufactured the NIC of the most active computer at the link level?
Use Google search to find the headquarters of the company that manufactured the NIC in the previous questions.
Palo Alto
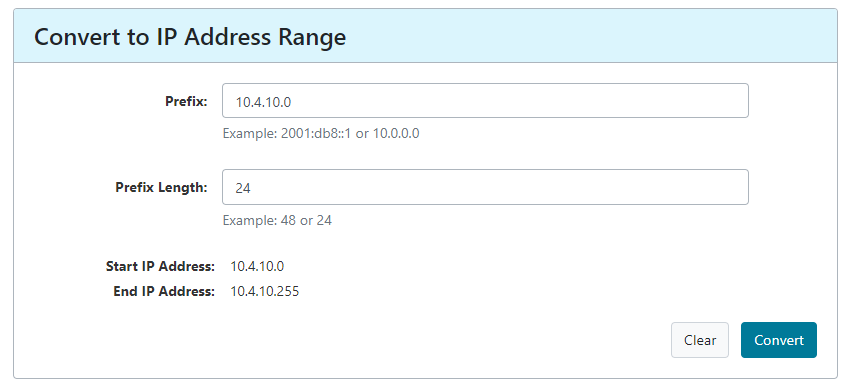
7) The organization works with private addressing and netmask /24. How many computers in the organization are involved in the capture?
My first thought after looking in Statistics → Endpoints was 4 computers because they looked similar, but I had no other rationale for the answer. This answer was incorrect.
I used my phone-a-friend lifeline and turned to Twitter for help (thanks @ihatesql!). As he helped me out, I started making connections back to doing Try Hack Me labs and attacking machines. When I ran nmap on a machine, I would run it on the entire network. In order to do that, I typed 10.4.10.0/24. This would catch all IPs in the network with a netmask of 24.
Then if we put the prefix we used above, 10.4.10.0, into a Classless Inter-Domain Routing (CIDR) calculator — you will have to Google that one! — and specify the netmask of 24 then it will show that the end IP address is 10.4.10.255. According to this article, https://www.ionos.ca/digitalguide/server/know-how/broadcast-address/, the last IP address is always the broadcast address, which is not a computer. Therefore our answer is 3!
3
8) What is the name of the most active computer at the network level?
Let’s turn back to the image from question 4. What should we look at for the network layer? IP Addresses!
The most active computer on the network level is 10.4.10.132. The question asks for the name of that computer though, which we can see through DHCP traffic. By searching ip.addr == 10.4.10.132 && dhcp we can see the host name once we expand Dynamic Host Configuration Protocol and Option: (12) Host Name. We could also search by the MAC address using eth.addr == 00:08:02:1c:ae && dhcp.
BEIJING-5CD1-PC
9) What is the IP of the organization's DNS server?
By searching dns, we can look at the response and see the IP of the DNS server by expanding Internet Protocol Version 4.
10.4.10.4
10) What domain is the victim asking about in packet 204?
Go to Go → Go to Packet… or press Ctrl + G. This will allow you to search for a specific packet. You can also type frame.number == 204 in the search bar. Expand Domain Name System and Queries to find the domain that the victim is asking about.
proforma-invoices.com
11) What is the IP of the domain in the previous question?
In the previous question, we looked at a DNS query. The goal of a DNS server is to convert a domain to an IP address so let’s expand and look at the Answers just underneath the Queries.
217.182.138.150
12) Indicate the country to which the IP in the previous section belongs.
Put the IP from the previous question into https://ipinfo.io/ to find the country to which it belongs.
France
13) What operating system does the victim's computer run?
When a computer sends a HTTP request such as GET, it sends information about itself through the user agent, such as the operating system and browser. This can be found in the User-Agent when expanding Hypertext Transfer Protocol.
Windows NT 6.1
14) What is the name of the malicious file downloaded by the accountant?
When we look at the GET request by searching http.request.method == GET then we can see the name of the malicious file.
tkraw_Protected99.exe
15) What is the md5 hash of the downloaded file?
I do not know a whole lot about virtual machines (VM) and disconnecting it from the network so I didn’t want to download malware for this question. I reached out to Twitter for some suggestions. One suggestion was to use https://any.run/ and the other was to read this book on building virtual machine labs https://leanpub.com/avatar2. I will learn more about this, but for now, I opted to Google “any run tkraw_Protected99” and find the report page below.
71826ba081e303866ce2a2534491a2f7
16) What is the name of the malware according to Malwarebytes?
I used Virus Total, https://www.virustotal.com/gui/home/search, to search by the md5 hash.
Spyware.HawkEyeKeyLogger
17) What software runs the webserver that hosts the malware?
We can find this by looking at the HTTP response from the webserver and expanding Hypertext Transfer Protocol.
LiteSpeed
18) What is the public IP of the victim's computer?
Go to Edit → Preferences → Appearance → Columns and check the box next to Host as seen above. When we search http then we can see the host bot.whatismyipaddress.com. Right click on this frame → Follow → HTTP Stream to see the IP of the victim’s computer.
173.66.146.112
19) In which country is the email server to which the stolen information is sent?
To see the destination of the mail server, we search for Simple Mail Transfer Protocol (smtp). We see the data being sent to the IP 23.229.162.69, which we can then put into https://www.abuseipdb.com/check/.
United States
20) What is the domain's creation date to which the information is exfiltrated?
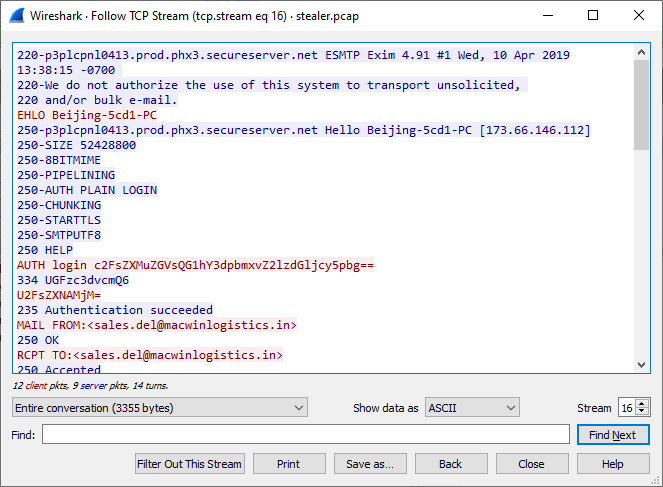
When searching smtp packets above, you can right click → Follow → TCP Stream to see the @macwinlogistics.in domain name. Then put that domain name into https://www.whois.com/whois/ to see the creation date.
2014-02-08
21) Analyzing the first extraction of information. What software runs the email server to which the stolen data is sent?
After going to right click → Follow → TCP Stream in the previous question, you can also see the software ran by the email server.
Exim 4.91
22) To which email account is the stolen information sent?
You can see this on the same screen as the above questions.
sales.del@macwinlogistics.in
23) What is the password used by the malware to send the email?
You can see the base64 encoded password used by the malware on the same screen as in the last couple questions above. Put that into https://gchq.github.io/CyberChef/ to see the actual password.
Sales@23
24) Which malware variant exfiltrated the data?
This is found within the same screen as the last couple questions above. Same as the last question, put it into https://gchq.github.io/CyberChef/.
Reborn v9
25) What are the bankofamerica access credentials? (username:password)
This is found within the same screen as the last couple questions above. Same as the last 2 questions, put it into https://gchq.github.io/CyberChef/.
roman.mcguire:P@ssw0rd$
26) Every how many minutes does the collected data get exfiltrated?
Search for smtp (Simple Mail Transfer Protocol) to see the data being sent through email every 10 minutes.
10